Experts warn every business will eventually fall victim to one of the new malware threats identified every day. Perhaps you haven't thought about a situation like ransomware before. You must ensure your critical data is adequately protected, but you must also take measures to recover it if it becomes corrupted or encrypted. It’s never a question of “if” it will happen to you; it is a matter of “when.”
But, backing up and recovering data isn't actually enough to maintain data security. Several new ransomware strains aim to delete backup files, agents, and security software. And while companies learned to leverage AI and bot tools for efficiency, these also became available to attackers to automate their own processes.
Much has happened since Dusty Koekenberg’s last ransomware blog post in November 2020. These are just a few:
Colonial Pipeline - As Joe Giordano, Program Director of the Touro College Illinois Cybersecurity, stated, “The Colonial Pipeline attack made such an impact because the pipeline is an important part of the national critical infrastructure system. Taking the system down disrupted gas supplies all along the East Coast of the United States, causing chaos and panic.” Attackers from the DarkSide gang have not been identified.
CNA Financial - After a Phoenix Locker/Hades ransomware attack, CNA Financial, a major insurance company, paid $40 million after a week of infection.
Technical University, Berlin - An attack shut down servers hosting their centrally managed Windows environment for a minimum of six weeks. Many services such as emails, their student portal, VPN client, and other applications were unavailable.
Red Cross - Half a million Red Cross records were compromised in January 2022 through a third-party contractor. Thousands of records were stolen, leaving people vulnerable. The attacker has yet to be identified.
Acer - Acer paid $50 million, the largest known ransom in history, in response to REvil’s attack, prompting enhancements to their cybersecurity infrastructure to protect business continuity and information integrity.
Kaseya - REvil paralyzed 1,500 organizations by compromising this tech-management software company. Two software flaws were exploited to access about 50 managed services providers (MSPs) that used its products. We can only guess if this prompted the company’s eventual purchase of Datto.
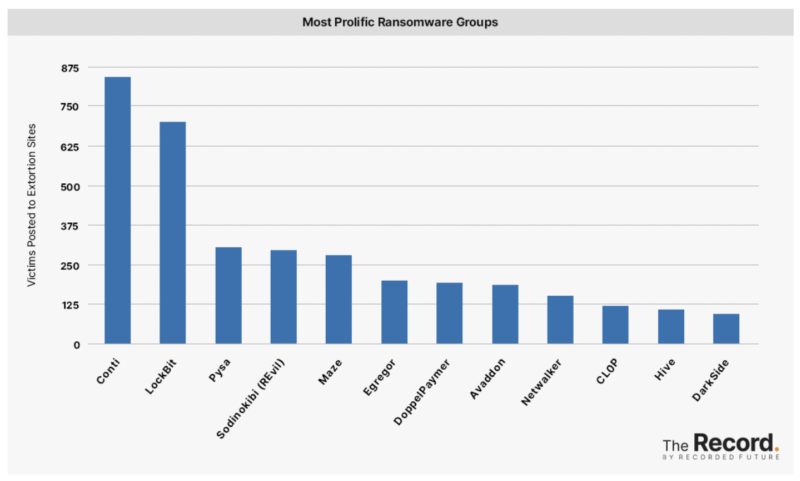
Source: https://therecord.media/ransomware-tracker-the-latest-figures/
Threats Today
Even though ransomware is becoming increasingly common, it isn't the only type of attack. Threats including malware, which shuts down operations or causes critical failures, denial of service attacks, which render products and services non-functional or unusable, and data breaches, which can steal valuable information, are becoming increasingly common.
Smaller businesses are especially vulnerable to these risks. According to the U.S. Small Business Administration, “88% of small business owners believed their business was vulnerable to a cyberattack.” Yet these are also the same companies without an in-house cybersecurity department, a security-focused MSP, or both.
The FBI’s Internet Crime Complaint Center reported 847,346 complaints of cyberattacks in 2021, leading to $6.9B in losses in the U.S.A. alone. IC3 reported only 3,729 ransomware incidents, a small number compared to what other security researchers track. This is likely due to the FBI's ability to only list incidents reported.
Being Proactive
Organizations should take a proactive approach to prevention to avoid becoming a victim of cyberattacks.
Knowledge - Cybersecurity training and testing breed caution among end-users by educating them about the risks. You minimize business risks when your employees know and understand the risks associated with their actions.
Recovery – There is nothing more powerful than being able to rapidly restore backup copies of your data, systems, and applications.
Technology - Cybercriminals are becoming institutionalized, utilizing advanced technologies and strategies to steal your information. Defend your endpoints with cutting-edge technologies and cybersecurity best practices.
Our New “Normal”
The last couple of years has, of course, changed the way we live and work. IT teams everywhere face complications with users bringing their own devices (BYOD), IoT, work from home (WFH), and distributed workforce across time zones and continents outside the regular infrastructure they’re used to managing.
Each of these creates potential new attack surfaces and methods that traditional security techniques can’t address. For example, a classic virus scanner or firewall won’t do much good if the attacked device is in a CEO’s home office.
An organization can't prevent a ransomware attack completely. But, organizations can mitigate the most damaging effects of a ransomware attack by improving their storage and data recovery systems in advance.
Hyperconvergence is an innovative way to simplify your IT operations and is more effective at protecting data than traditional systems. A properly architected HCI solution radically reduces the attack surface by eliminating storage protocols and not simply virtualizing SANs. Storage protocol-based attacks simply won't work with HCI infrastructure.
Ransomware can sit dormant for weeks, if not months. We get constant feedback from our customers that they sleep easier knowing Scale Computing's software and hardware solutions have integrated ransomware protection - because we do things differently.
Want to know how? Download our eBook.

